I wrote a post about using Functions’s Managed Identity to connect with Dataverse back in Nov, 2021. In that post I used Bicep only. But the technology landscape has advanced since then. I have now rejigged the codebase and used Azure Developer CLI along with Power Platform CLI.
Azure Developer CLI makes it super easy to create/update resources into Azure and deploy Function code as well. You’ll just need to remember three commands.
- azd up – Creates/updates resources and deploys application code
- azd provision – Only creates/updates resources in Azure
- azd deploy – Only deploys application code
The amazing part about azd is that there are hooks. You can run PowerShell code for various events along the deployment. There are 16 hooks available, but in this repo I just had to use pre-deploy, post-deploy and post provision hooks. The hooks themselves get the azd environment variables injected into the context, so you can easily access them inside your PowerShell script.
In order to provision this template and Function code to your tenant you’ll first need to run
azd init -t rajyraman/PowerApps-Managed-Identity-Demo-FunctionsThis will get all the repo contents to your local machine (sort of like git clone), and then you can run
azd upazd will now try to grab all the variables that are need for the deployment. The variables are declared in the main.parameters.json file.
{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"environmentName": {
"value": "${AZURE_ENV_NAME}"
},
"location": {
"value": "${AZURE_LOCATION}"
},
"serviceEndpointStorageLocations": {
"value": "${SERVICE_ENDPOINT_STORAGE_LOCATIONS}"
},
"createVNet": {
"value": "${CREATE_VNET}"
},
"createPrivateLink": {
"value": "${CREATE_PRIVATE_LINK}"
},
"dataverseUrl": {
"value": "${DATAVERSE_URL}"
}
}
}This is a sample .env file I have as my dev config, so that you know what sort of values are expected.
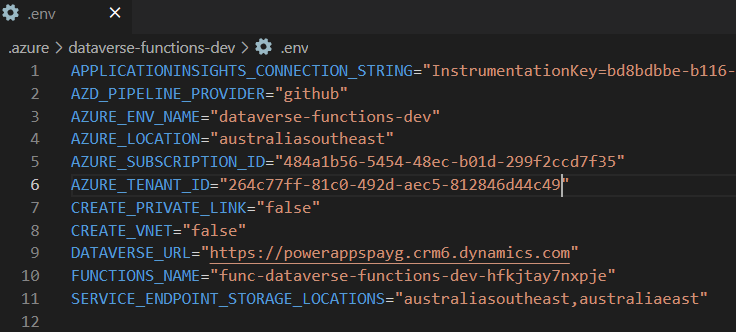
The repo can be deployed in three possible configurations.
- Function App in Consumption plan with no VNet
- Function App in Elastic Premium with just VNet and Storage Endpoint
- Function App in Elastic Premium with just VNet and Private Link
All these three configs are dictated by the CREATE_VNET and CREATE_PRIVATE_LINK environment variables. Creating the Function App’s Service Principal as an application user and giving it System Administrator role is run as part of post-provision hooks. So, there is no need to do this manually.
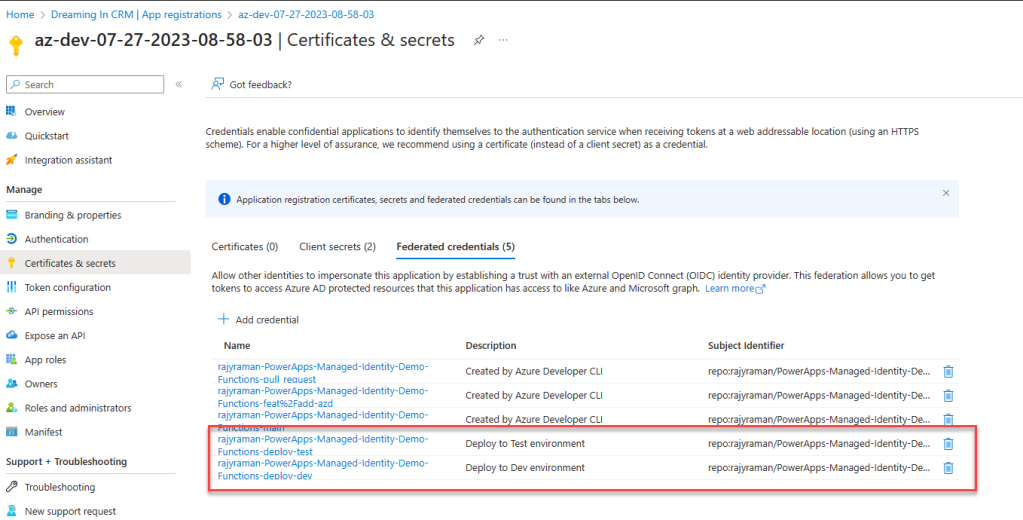
I have also tweaked the default workflow that azd pipeline config creates and added GitHub environments into the mix. The additional change this entails is that you’ll have to add the environments into the Federated Credentials.
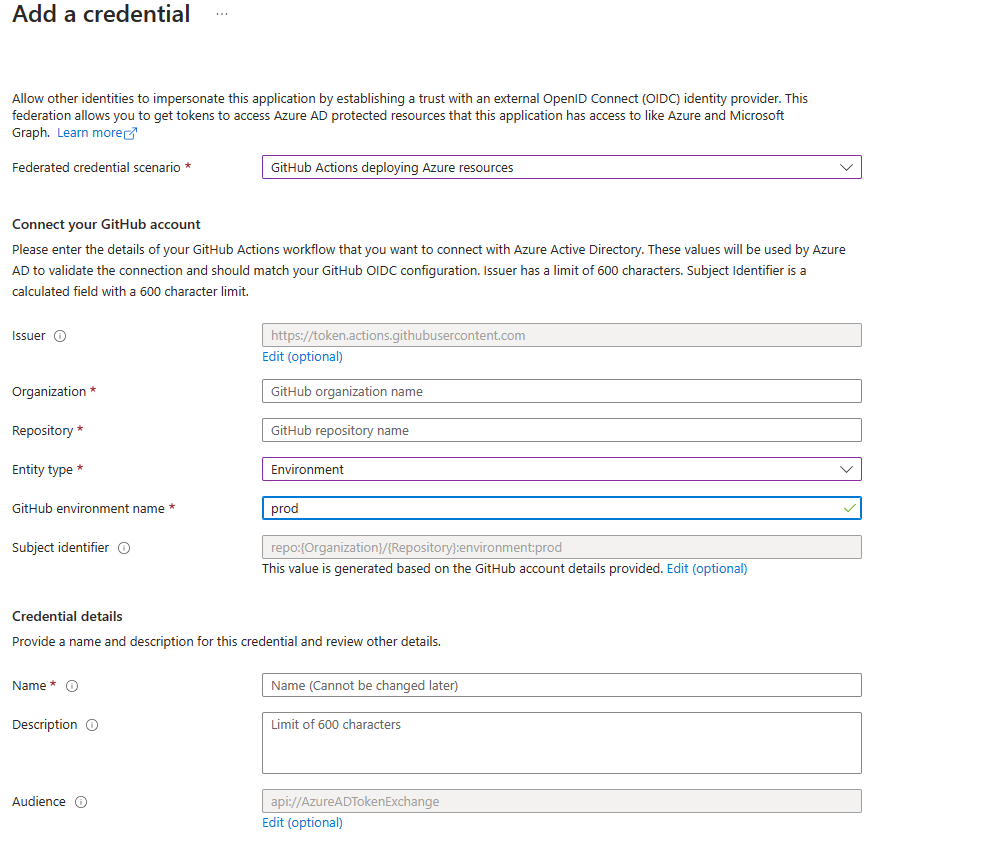
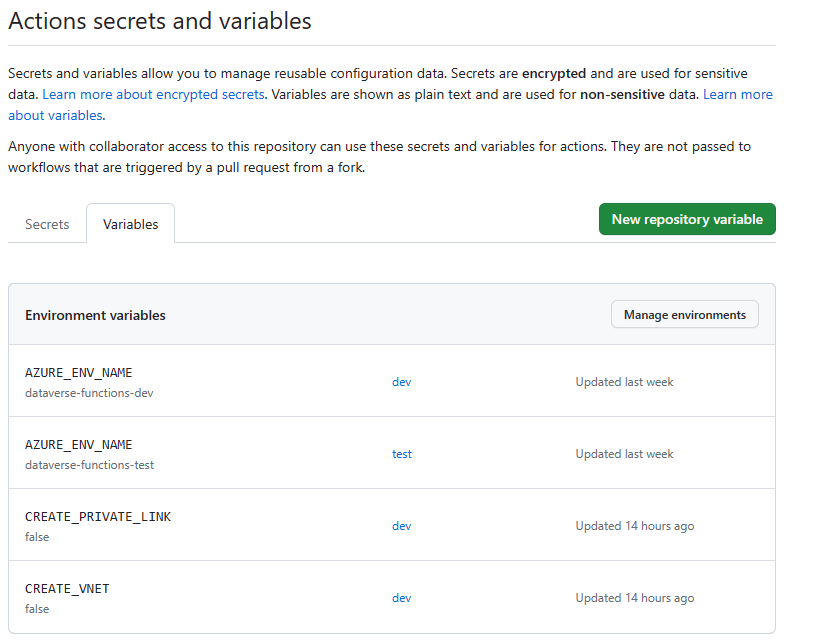
This means you can now create environment specific variables and secrets in GitHub.
I hope this post serves as a starting point to deploy Functions that interact with Dataverse.
Repo: https://github.com/rajyraman/PowerApps-Managed-Identity-Demo-Functions
References:
[…] (08-Aug-23): Refer to https://dreamingincrm.com/2023/08/08/connecting-to-dataverse-from-function-app-using-managed-identit…for latest approach using […]